Security and cryptography libraries for embedded systems
– Security and Cryptography are essential for all embedded systems.
Whether you want to protect your IP against counterfeiting, your devices against manipulation or data collected on the devices against snooping, SEGGER’s Embedded Experts got you covered.
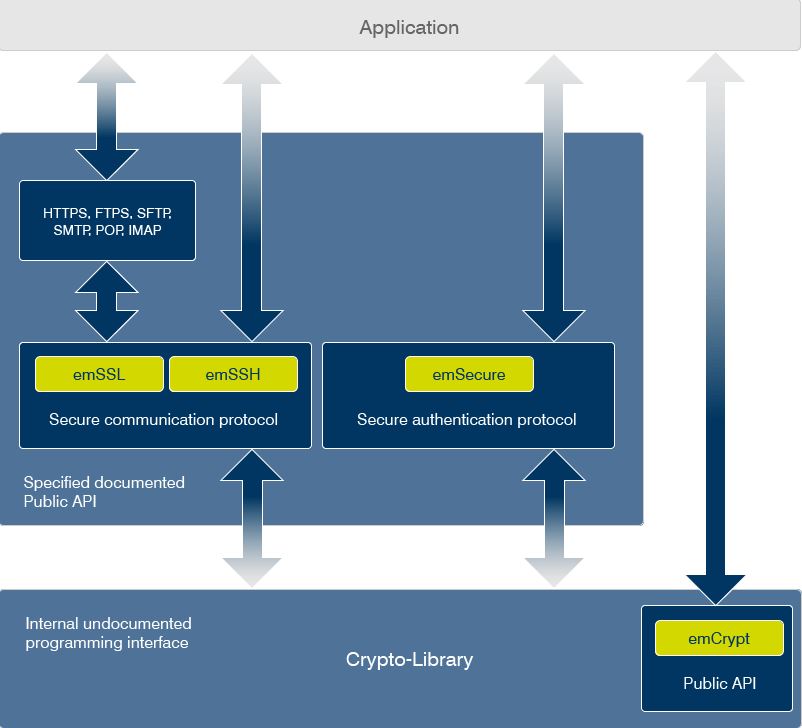 SEGGER’s cryptographic and security libraries have been built from the ground up for embedded systems. The resulting libraries are extremely fast and use little resources in memory. You can select whether you want to use a protocol, that already is fully implemented such as SSH (emSSH), and TLS (emSSL), or you can pick emCrypt and create your own security protocol based on proven, state of the art algorithms.
SEGGER’s cryptographic and security libraries have been built from the ground up for embedded systems. The resulting libraries are extremely fast and use little resources in memory. You can select whether you want to use a protocol, that already is fully implemented such as SSH (emSSH), and TLS (emSSL), or you can pick emCrypt and create your own security protocol based on proven, state of the art algorithms.
Crypto & Security
– Security libraries optimized for embedded systems
 Secure your device and stop cloners
Secure your device and stop cloners
emSecure is a software solution to securely authenticate digital assets. It can be used to secure products at no per unit cost against hacking and cloning.
 Reliable, secure and build for IoT devices
Reliable, secure and build for IoT devices
emSSL is software library that enables secure connections across the Internet. emSSL offers both client and server capability. SSL/TLS is a must-have in nearly every application which is connected to the Internet. Products of the IoT, smart grid or home automation markets benefit from securing their communication.
 Dedicated, fast algorithms
Dedicated, fast algorithms
The emLib product family offers extremely efficient single purpose modules for AES-, and DES-encryption, as well as CRC-checksums.
Provide security for the administration interface of your device
emSSH is a software library that enables secure login to your embedded system. emSSH offers the possibility to establish a secured connection to any server application in your product. It can be used both target independent in native computer applications, as well as in embedded targets.
 Create reliable security protocols
Create reliable security protocols
emCrypt is a stat-of-the-art cryptographic algorithm library that scales well from resource-constrained devices, such as deeply embedded systems to workstations. It is ideally suited to create security protocols.
 Secure your device and stop cloners
Secure your device and stop cloners Reliable, secure and build for IoT devices
Reliable, secure and build for IoT devices Dedicated, fast algorithms
Dedicated, fast algorithms
 Create reliable security protocols
Create reliable security protocols